Targeted cyber-attacks are specially design to infect a particularly person, business or industry. Although untargeted attacks are more common, targeted attacks still are more destructive and can cause significant losses. While untargeted attacks are not made for particular business or person and this type of cyber-attacks aim to infect as many businesses and people as possible, targeted attacks are hand-picked and tailored for the specific target and goal - most often to make money or paralyze the target.
Many companies have experienced data loss and downtime as a result of a ransomware attack. Large companies to whom IT supports business operations usually are the most desired target of ransomware, because they are capable to pay the requested amount of money and their downtime can lead to significant loss in revenue. One of the latest attacks occurred to well-known company Garmin1 that is one of the largest GPS navigation and wearable technology for the automotive, aviation, marine, fitness, and outdoor markets businesses. Targeted WastedLocker ransomware caused several day outage not only for web applications, but also for call centers disabling receipt of any calls, emails and online chats. Garmin customers around the world couldn’t connect to their Garmin services, causing frustration and confusion, as well as fear about their personal data security. Information about total losses currently is not available, but we can observe it negatively affected the value of the brand. This ransomware has already been uploaded in antivirus platform, making protection against it available the same day Garmin has been infected.
Statistics show that the average cost of ransomware-caused downtime per incident was 141 000 dollars in 2019 and is predicted to double in 20202. These numbers should increase your willingness to invest in necessary resources to protect your business against ransomware.
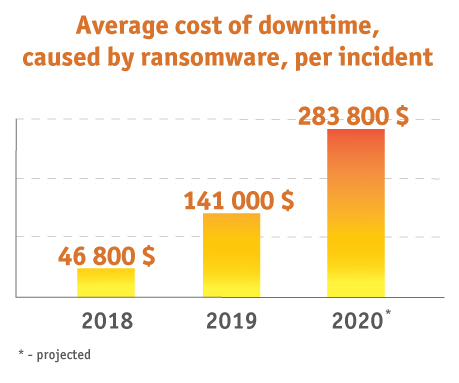
Source: SafetyDetectives
How to reduce impact of a ransomware?
There are only few actions that you can do to reduce the impact of ransomware, when it has already reached you or your business. You will not be able to avoid data or money losses in this case, but you can decrease it, if act fast, wise and coordinated. These actions include total shut-down of systems, servers and network to reduce the spread of ransomware, as well as in-depth IT knowledge will be required in order to bypass ransomware and resume operations, if possible. However, many targeted ransomware attacks are designed to encrypt its target files and, as they are specially made for specific person, company or industry, they are able to destruct their particular target. In other words, hackers have invested a lot more time to explore its target systems in order to customize the ransomware, that’s why you may not be able to restore infected data and systems after the attack.
Preventive actions will cost you less
Malicious emails, attachments, fake webpages and even fake system update pop-up windows are the most used forms of hidden virus packages to call user action. When the ransomware has been downloaded, it begins its work to infect not only your device, but also all devices connected to the network. Users play an important role, allowing the virus to enter the system, that’s why investing in their trainings should not be postponed.
1. Security awareness training for your employees
Knowledge about dangerous threats and a level of preparedness are key elements for your confidence that your employees will be able to detect any threat quickly. You will save a lot of time if your employees will know what steps they need to perform when a virus is detected. Cybersecurity training will let them recognize, report real attacks, as well as behave accordingly. Don’t forget about simulations, because only practical tests can highlight how ready your employees are.
Cybersecurity trainings should not be limited to technical staff. Employees from all other structures must be educated as well, because the overall level of cyber-hygiene will determine how easy or difficult target you are. Share information about malicious emails, how to detect them and what to do when you receive them. Share the latest attack trends and how to stay secure. Share information how important it is to change passwords and not to spread internal information externally. Even if you think that everyone knows this information, a reminder won’t let your staff to forget it and will keep them informed and ready.
2. Offline data backup
 Data backups can save your business in many situations. Accidentally deleted data or hardware failure - in both situations you will be able to restore data from backup copies in order to minimize downtime and increase continuity level. Online backup is the most common backup type – businesses choose backup frequency, data amount and data retention period. Automated data backup software creates backups and restore when necessary. However, online backup copies will not protect your business when a virus or ransomware attack strikes.
Data backups can save your business in many situations. Accidentally deleted data or hardware failure - in both situations you will be able to restore data from backup copies in order to minimize downtime and increase continuity level. Online backup is the most common backup type – businesses choose backup frequency, data amount and data retention period. Automated data backup software creates backups and restore when necessary. However, online backup copies will not protect your business when a virus or ransomware attack strikes.
Maintaining only online backup system is the most common mistake companies make. When a virus is uploaded in your system, it will infect all devices and systems that are connected to your network. Having backup system and copies available in the same network will result in an encryption of your backup data as well. Offline backup is necessary to stay fully secured. Offline backup copies are not created as frequently as online ones and when a virus is detected, an employee responsible for turning off any coming backup performance will decrease the risk of copying infected files to your backup systems and increase your chances to quickly restart your business from created backups.
3. Up to date antivirus and security system
There are many viruses, worms, Trojans, as well as ransomware in a digital environment. New and improved previous ones are created to bypass security systems. Antivirus and security systems are constantly improving their operations in order to repel new types of cyber-attacks. Not performing the latest updates can cost you a lot more in case of an attack. Not only up to date security system, but also up to date operating system and software are very important, because many cyber-attacks are based on software vulnerabilities as well. Software versions are not always easy to track down in case of a company with hundreds of employees, that’s why a special centralized management software can help you with that. For example, Microsoft SCCM tool is a great help to not only monitor all your employee workstations and systems, but also perform any necessary updates.
4. Up to date antispam system for emails
Special attention should be paid to antispam systems, because emails are the most used source to spread viruses. Antispam system will let you build a shield that will not let malicious emails thru and, doing so, minimize the possibility that your employees will open an infected email. As mentioned above, viruses and ransomware are changing very quickly, so keep your antispam up to date in order to minimize risks of cyber-attacks.
5. Computer configuration in accordance with the best security practices
Disallowing to download files from internet, install software, as well as setting up regular password change obligation and alerts for unusual digital activities of employees can all help reduce risk of cyber-attacks. The best protection is to combine different conditions and settings, that’s why an overall plan will help you to find and maintain configuration your company needs.
Minimize the risk using complex solutions
There is not one 100% secure method to protect your business from ransomware. Combine all suggestions mentioned above in accordance with your specific business capabilities in order to minimize this risk and to be able to respond quickly in case of a cyber-attack. Most of preventive protection activities are not very complicated and expensive to implement. Don’t wait when the attack strikes your business, take action now and protect yourself from unforeseen expenses or data loss.
Back
