DDOS PROTECTION & MITIGATION SERVICE
Protect your online services from unwanted attacks and avoid downtime of your online applications with DoS Attack Protection and DDoS Protection Service!

Business continuity up to 99.995%
DoS protection and DDoS mitigation automatically detects attacks and blocks known attack patterns

Protection for all your IT infrastructure
Our DoS attack protection and DDoS protection services defend against known attack patterns across entire infrastructure

Uninterrupted customer experience
We ensure your network is always up and running, maintaining excellent user response time even when under attack
24/7 service is designed to protect infrastructure and customer online processes against different types of DoS and DDoS attacks that are on the rise and over the past few years have evolved into complex and overwhelming security challenges for organizations of any size. Have you considered the average hourly cost of downtime for your business?
Protect your business applications and servers from the latest and even the largest attacks and vulnerabilities with DoS attack protection and DDoS mitigation service!
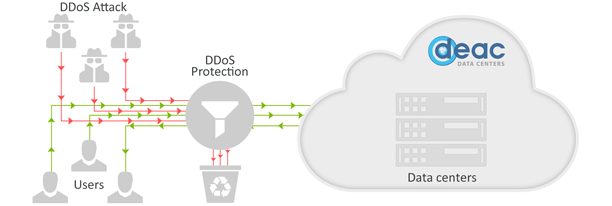
The most common target of malicious attacks are websites - high volume traffic overloads web server to make the service very slow or even unreachable to users. With the development of Internet-of-Things (IoT), security issues have even more significant impact than ever as insecure devices can be easily used for distribution of attacks.

Avoid reputation and financial losses
Avoid disruptions and glitches of your business services caused by cyber-attacks with DoS protection and DDoS mitigation provided by secure DEAC data centers!
Protection against multiple attack types
Anti-DDoS protection service is centrally distributed through DEAC’s network and protects against multiple attack types, with a single point of contact delivering equipment and service.

Keep your business traffic unaffected
DoS and DDoS protection service neutralizes flooding attacks within milliseconds of emergence by rapidly detecting, filtering and blocking DDoS packets, while allowing legitimate business traffic to flow unimpeded.
Protection that always keeps your business processes available
DoS protection and DDoS mitigation service clears attack traffic before it reaches the company's Internet pipe, protecting against downtime and service degradation.
Complex data security solutions for complete security
We will help to evaluate level of security for your enterprise and will create an individual disaster recovery plan that includes not only DoS protection and DDoS mitigation, but also backup solution to avoid important data loss.
Risk diversification
Maintain duplicate IT infrastructure choosing the most suitable data center location according to your requirements and always be ready to recover your IT system in case of an attack, data loss or other disaster!
Contact us to find out more
DoS and DDoS attacks
Types of DoS and DDoS
mitigation
Technical specification
A Distributed Denial of Service (DDoS) attack uses many hijacked computers around the world to send coordinated requests against one or more targets and floods a website or application with a high volume of traffic, causing crash of servers or their inability to operate. DoS attack is a Denial of Service attack, which uses one computer and Internet connection to overload server or other IT resources.
Depending on your preferences for the level of protection, we offer two types of DoS and DDoS mitigation service. Each DDoS mitigation service has adaptable options, for more detailed technical specification find information below. Choose the most suitable DoS and DDoS mitigation plan to suit your business needs or get personal security advice from DEAC experts!
 |
Volume DDoS protection – created to mitigate attacks, which produce high amount of traffic to overload and deny services. Using DEAC volume anti-DDoS your network infrastructure will be safe and protected. |
 |
Smart DDoS protection – your advanced protection against both volume and smart attacks, which try to exhaust server resources by exploiting their vulnerabilities. Protect your server from attacks like TCP SYN Flood, Slow-Read attack, HTTP GET/POST flood, Zero-Day vulnerabilities and others. |
- Early detection with 24/7 monitoring and reporting tools of DoS and DDoS mitigation service and real-time email notifications
- Anti-DDoS protection service automatically detects attacks and blocks known attack patterns including network attacks, protocol attacks and application attacks
- Under 5% false-positive incidents during DDoS attack mitigation
- 1000 Gbps passive bandwidth – determined IP packet processing without establishing TCP connection
- Over 300 Gbps active bandwidth – every incoming TCP connection is processed and analyzed
- Added latency, when traffic proxying is used – 0 to 100 ms. In case HTTP traffic comes through the proxy due to using persistent HTTP connections with your protected service, there is a possibility of increase in its performance
|
|
VOLUME DDoS protection |
SMART DDoS protection |
|
DDoS mitigation service includes |
Defends your network infrastructure against volume traffic per single IPv4 address. |
Mitigates both volume & smart attacks with HTTP filtration (per single service). |
|
You can choose |
- number of IPv4 addresses - Clean downlink bandwidth |
- number of IPv4 addresses - Clean downlink bandwidth - Dirty downlink bandwidth |
FIND OUT MORE ABOUT OTHER SOLUTIONS:
FAQ
DoS or DDoS can attack almost any business, which means it is better to take precautions before it happens. Usually online business like e-commerce, finance service, gaming and other industries consider DoS and DDoS protection as a must-have.
DoS attack is a Denial of Service attack, which uses a computer with Internet connection to cause server unavailability. Server’s resources are being overloaded with TCP/UDP packets. However, DDoS attack will use many computers and devices known as botnets to cause a larger harm. Request our IT experts DoS attack protection and DDoS mitigation service included in one!
We offer two types of DDoS protection – from volume and smart attacks. For example, smart attacks are more sophisticated and a higher level of protection is required. These include Slow-Read attacks, TCP SYN Flood, Zero-Day vulnerabilities, HTTP GET/POST floods and many other types. DDoS attacks evolve rapidly; hence, we suggest choosing most up-to-date DoS protection and DDoS mitigation service.
DEAC IT experts will provide necessary advice on the latest protection systems – just contact us!